 Are TAs expected to develop mobile apps?
Are TAs expected to develop mobile apps?
No, they are not. However they are expected to understand pros, cons and risks associated with mobile platforms. TAs are expected to create mobile strategies while designing mobile solutions. Based on requirements, TAs are expected to zero-in on correct mobile strategy.
Why go Mobile?
Mobile apps are no longer an option, they’re a necessity now. People around the world are spending more time using mobile apps than browsing internet over their laptops or smartphones (can now be nicknamed “app phones” 🙂 )
Many enterprise companies have realized this and are now focusing on going mobile as well. And they are now willing to make their flagship products/services, available on mobile devices.
What’s inside Salesforce.com mobile SDK?
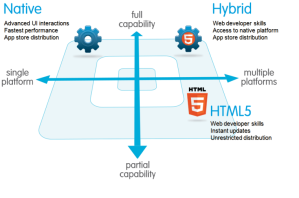
Salesforce’s Mobile SDK provides three Mobile Application Development options.
- Native apps are specific to a given mobile platform (iOS or Android) using the development tools and language that the respective platform supports (e.g., Xcode and Objective-C with iOS, Eclipse and Java with Android). Native apps look and perform the best.
- HTML5 apps use standard web technologies—typically HTML5, JavaScript and CSS. This write-once-run-anywhere approach to mobile development creates cross-platform mobile applications that work on multiple devices. While developers can create sophisticated apps with HTML5 and JavaScript alone, some vital limitations remain at the time of this writing, specifically session management, secure offline storage, and access to native device functionality (camera, calendar, geolocation, etc.)
- Hybrid apps make it possible to embed HTML5 apps inside a thin native container, combining the best (and worst) elements of native and HTML5 apps.
Deciding factors
At times choosing the right option might get tricky. But if your requirements are clear and you are absolutely sure what you want? Then it becomes much easier to pick the right option. While working on your mobile strategy you will have to base your decisions on following factors (but not limited to)
- Platform (IOS or Android)
- Your development team’s skills.
Could include HTML5, Javascript, CSS, Java, Eclipse, etc… - Access to native components (like camera, calendar, etc.)
- Offline Data Storage capabilities.
A must have feature when you want your users to be able to work even without internet access. And can synch whenever internet access is available.
Here are some useful links:
http://wiki.developerforce.com/page/Mobile
http://wiki.developerforce.com/page/Webinar:_IntroMobileSDK
Hope that’s helpful.